The Standard HTLC Flow
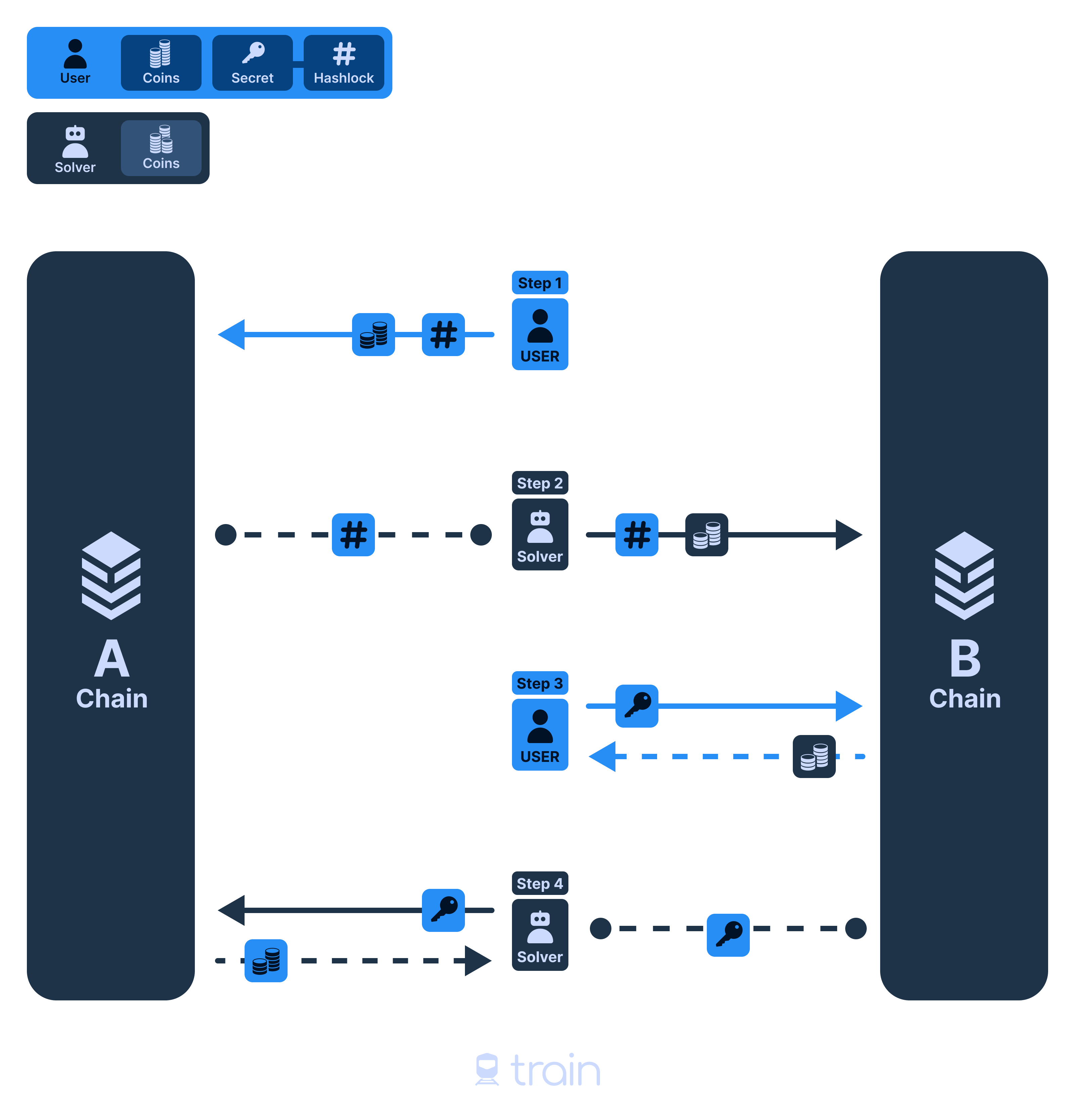
User Lock
The User generates a Secret S and computes Hashlock HASH(S). Then, they create an HTLC, locking funds for the selected Solver in the Source Network.
Solver Lock
The Solver detects this HTLC and creates a counterparty HTLC with the same Hashlock. This locks funds for the User (initial amount minus the Solver Fee) in the Destination Network.
Challenges with HTLCs
Despite their potential, HTLCs have proven impractical for real-world bridging due to three main issues:- Secret Management: Users must generate and securely manage a Secret until the counterparty completes their transaction.
- Claim Transaction on the Destination Network: Users may lack assets on the Destination Network, especially if it’s their first time interacting with that Network.
- Liveness: Users must maintain the state of the bridging process locally and actively monitor and respond to counterparty transactions.